Our Microsoft Cloud Security solutions provide end-to-end protection across your cloud environments, ensuring compliance, detecting threats, and managing risks in real time.
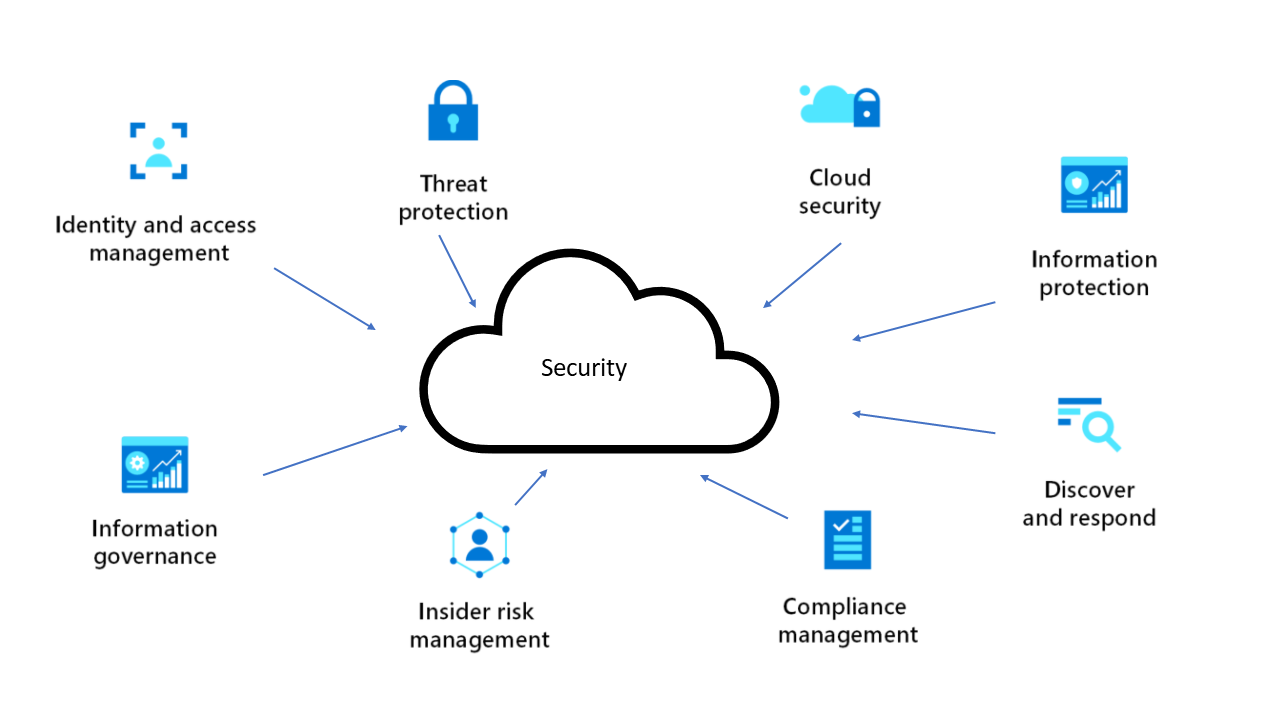
Microsoft Cloud Security offers an integrated approach to securing data, applications, and workloads in Microsoft’s Azure environment. With Microsoft Cloud Security tools, businesses can maintain secure access, monitor for suspicious activities, and protect assets from emerging cyber threats.
Microsoft’s security features, including Microsoft Defender, Identity and Access Management, and Secure Score, help enterprises implement security policies that mitigate risks while enhancing compliance with industry standards.
Microsoft’s AI-driven threat detection tools prevent, detect, and respond to complex attacks, providing robust protection for sensitive cloud data.
Stay aligned with regulatory standards like GDPR, HIPAA, and PCI DSS, using Microsoft’s compliance tools and continuous security monitoring.
Leverage advanced identity management and data encryption tools to ensure data privacy and protect against unauthorized access.
Our assessment process ensures a complete evaluation of your security posture in the Microsoft Cloud. Here’s how we do it:
We assess your current Microsoft Azure environment, understanding your security needs and identifying initial vulnerabilities.
Our experts review your security policies and configurations to align with best practices and regulatory requirements.
We conduct simulated attacks and monitor responses to ensure robust defense mechanisms are in place.
Using Microsoft Secure Score, we analyze your system's risk level and provide insights to improve your security posture.
We create a tailored security improvement plan with actionable recommendations for protecting your Microsoft environment.
After the assessment, we offer continuous monitoring to detect new threats and support security policy updates.
Contact our team today to learn how Microsoft Cloud Security can protect your assets and enable safe, compliant operations in the cloud.
Contact Us© Apex Cyber Safe. All Rights are Reserved.